Experiencing issues with your website’s control? You might be facing session hijacking. This occurs when hackers intercept and take over active sessions, compromising your data. How To Prevent Session Hijacking? Implement security measures like encryption and secure cookies, and regularly update your software. Stay one step ahead to keep your online presence secure.
What is a session ID?
A session ID is like a special passcode given to you when you visit a website. It helps the website remember who you are as you move around it. It’s like a ticket that lets you access different parts of the website without having to sign in again each time.
For example: Imagine you’re visiting an online store. When you first arrive, the store gives you a special passcode called a session ID. As you browse the store, adding items to your cart and checking out, you don’t have to keep proving who you are because the website remembers you using that session ID. It’s like having a virtual ticket that makes your shopping experience smoother without constantly needing to log in.
What is Session hijacking?
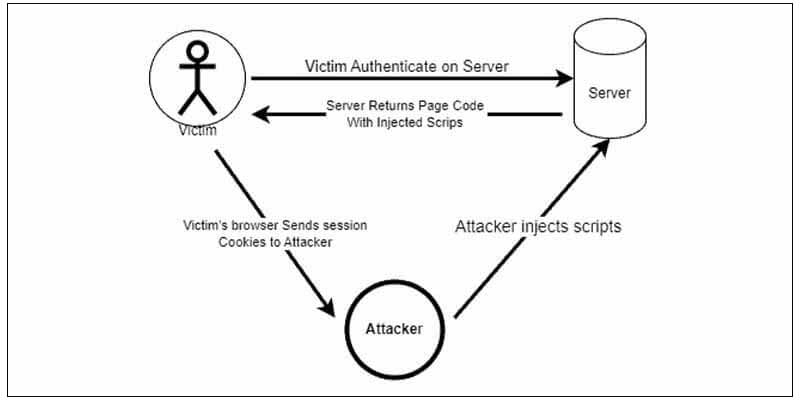
Session hijacking is a stealthy cyberattack where an unauthorized user intercepts and takes control of an ongoing session between a user and a website or application. This nefarious act grants the attacker access to sensitive information and privileges. To safeguard against such breaches, it’s crucial to implement robust security measures. Session hijacking prevention includes utilizing encryption protocols, employing secure cookies, and regularly updating software for enhanced protection.
How does session hijacking work?
Attackers employ various methods to intercept session IDs, enabling them to gain unauthorized access to user sessions. Once control over the session is obtained, attackers can engage in malicious activities such as extracting sensitive information, conducting unauthorized transactions, or modifying account settings, and even escalating their privileges within the system.
Several common techniques are used in session hijacking:
Session Sniffing:
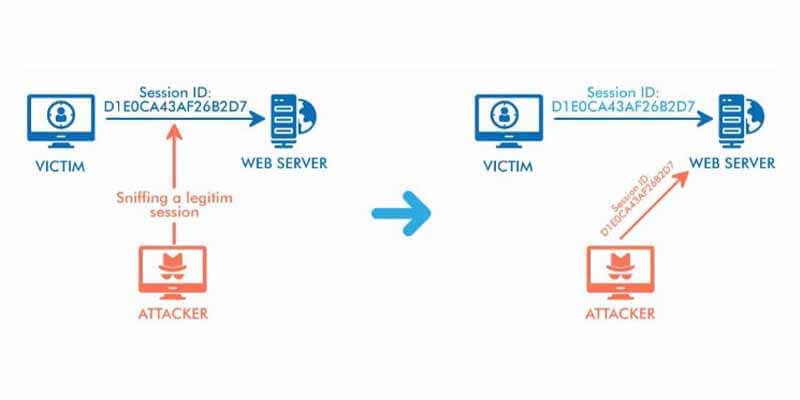
Also known as session side-jacking, this active hijacking technique targets the insecure transmission of session IDs. While most websites encrypt login pages for password security, some leave other pages unencrypted. Attackers use packet sniffing tools to monitor network traffic and capture session cookies after authentication, enabling them to impersonate users on unencrypted pages.
Cross-Site Scripting (XSS):
In XSS attacks, threat actors manipulate vulnerable websites by injecting client-side scripts to bypass the same origin policy. These scripts execute malicious code, typically JavaScript, designed to capture session IDs. Despite the appearance of legitimacy, the page loads content from a trusted server, facilitating session hijacking.
Session Prediction:
Some websites follow predictable patterns for generating session IDs. Attackers capture valid session IDs and analyze them to understand the session ID generation algorithm. Once the algorithm is deciphered, attackers may predict and generate valid session IDs to target specific users.
Session Fixation Attacks:
Instead of intercepting session IDs, attackers generate or steal a valid session ID from the target website before users enter login credentials. Users are then tricked into using the compromised session ID, allowing attackers to access the session after authentication.
Malware:
Malware is a common method used to steal browser information, including session IDs. Once installed, malware can quickly steal information, including session IDs, within seconds, as demonstrated by Linus Sebastian in the linked video.
Why Is Session Hijacking Dangerous?
Session hijacking poses a severe risk to website security, potentially causing irreparable harm to both users and the website itself. When a hacker successfully hijacks a session, what are the potential dangers that ensue?
Unauthorized Access to User Information:
By hijacking a session, hackers gain access to the user’s account details, including login credentials, personal data, and transaction history. This information can be exploited for identity theft, financial fraud, or other nefarious purposes.
Loss of Sensitive Data:
Attackers can exploit session hijacking to pilfer sensitive data such as credit card information, personal details, or confidential business data. Such breaches not only harm users but also tarnish the reputation of the website and may lead to legal and financial repercussions.
Potential Fraudulent Transactions:
Session hijacking grants attackers control over the user’s account, enabling them to initiate fraudulent purchases or transactions. This can result in financial losses and damage the reputation of both the user and the affected website.
Difficult to Detect:
The stealthy nature of session hijacking makes it challenging for users to identify. Since hackers can manipulate user accounts without leaving obvious traces of intrusion, victims may remain unaware of the compromise until significant damage has occurred.
Risk Factors and Vulnerabilities
Session hijacking risks compromising user sessions through intercepted data, weak authentication, and session management flaws. Mitigate these risks with secure encryption, robust authentication, and diligent session management practices. Let’s learn what kind of risk factors and vulnerabilities could be posed if session hijacking happens.
Unencrypted Connections:
Sessions transmitted over unencrypted connections, such as HTTP instead of HTTPS, are vulnerable to interception. Attackers can employ network sniffing techniques to eavesdrop on communication between the user and the server. Without encryption, session data including cookies, credentials, and other sensitive information can be easily intercepted, allowing attackers to hijack sessions and gain unauthorized access to user accounts.
Weak Authentication:
Weak authentication mechanisms, such as simple passwords or lack of multi-factor authentication, make it easier for attackers to compromise user accounts. If an attacker can guess or crack a user’s password, they can impersonate the legitimate user and hijack their session. Additionally, compromised credentials obtained through data breaches or phishing attacks can be used to gain unauthorized access to sessions.
Session Management Issues:
Inadequate session management practices can introduce vulnerabilities that attackers can exploit to hijack sessions. For example, failing to properly expire or invalidate session tokens after a user logs out or after a certain period of inactivity can allow attackers to reuse session identifiers to impersonate legitimate users. Similarly, if session tokens are not securely generated or are predictable, attackers can guess or brute-force session IDs to hijack sessions.
Cross-Site Scripting (XSS) Attacks:
Cross-Site Scripting (XSS) vulnerabilities occur when web applications fail to properly sanitize user input, allowing attackers to inject malicious scripts into web pages viewed by other users. These scripts can then execute in the context of the victim’s browser, enabling attackers to steal session cookies or perform actions on behalf of the victim. By hijacking a user’s session, attackers can gain unauthorized access to sensitive data or perform malicious activities, such as account takeover or fraud.
Man-in-the-Middle (MitM) Attacks:
In a Man-in-the-Middle (MitM) attack, an attacker intercepts communication between the user and the server, allowing them to eavesdrop on or modify the transmitted data. By positioning themselves between the user and the server, attackers can capture session cookies, credentials, or other sensitive information exchanged during the session. With this information, attackers can hijack the session and impersonate the legitimate user, potentially gaining access to sensitive resources or performing unauthorized actions.
Session Fixation:
Session fixation is a vulnerability that occurs when an attacker forces a user to use a predetermined session identifier. This can be achieved by tricking the user into clicking on a malicious link containing a session ID or by manipulating session management mechanisms. Once the user’s session is fixed to a known identifier controlled by the attacker, they can hijack the session by using the same session ID to authenticate as the legitimate user. This allows attackers to bypass authentication mechanisms and gain unauthorized access to the user’s account.
Insecure Session Handling:
Insecure session handling practices, such as using predictable session IDs or insufficient session timeouts, can expose sessions to hijacking attacks. Predictable session IDs make it easier for attackers to guess or brute-force valid session identifiers, while insufficient session timeouts allow inactive sessions to remain valid for longer periods, increasing the window of opportunity for attackers to hijack them. Additionally, failing to properly secure session data stored on the client-side, such as in cookies, can expose sessions to theft or manipulation by attackers.
In summary, session hijacking remains a significant threat to online security, exploiting vulnerabilities in authentication and session management. Implementing robust security measures is essential to safeguard against this malicious practice and protect user data from unauthorized access.
How Can We Prevent Session Hijacking Vulnerabilities?
If we are able to prevent the vulnerabilities and risk factors, we can protect our site from hijacking. Once a site is infected, you will have to suffer a lot. Sometimes the hackers may blackmail you and demand money.
That’s why, to prevent session hijacking vulnerabilities, it’s essential to implement the following measures:
Encryption: Utilize HTTPS to encrypt communication between the client and server, preventing attackers from intercepting sensitive session data.
Strong Authentication: Implement robust authentication methods such as multi-factor authentication and strong password policies to prevent unauthorized access to user accounts.
Secure Session Management: Employ secure session handling practices, including generating random and unpredictable session identifiers, properly expiring sessions after a period of inactivity, and securely managing session data on the server side.
Input Sanitization: Thoroughly validate and sanitize user input to mitigate Cross-Site Scripting (XSS) vulnerabilities, preventing attackers from injecting malicious scripts into web pages to steal session cookies.
Network Security Measures: Implement network security measures such as firewalls, intrusion detection systems, and virtual private networks (VPNs) to detect and prevent Man-in-the-Middle (MitM) attacks.
Regular Security Audits: Conduct regular security audits and vulnerability assessments to identify and remediate potential session hijacking vulnerabilities proactively.
Implementing IP Filtering and Session Timeouts:
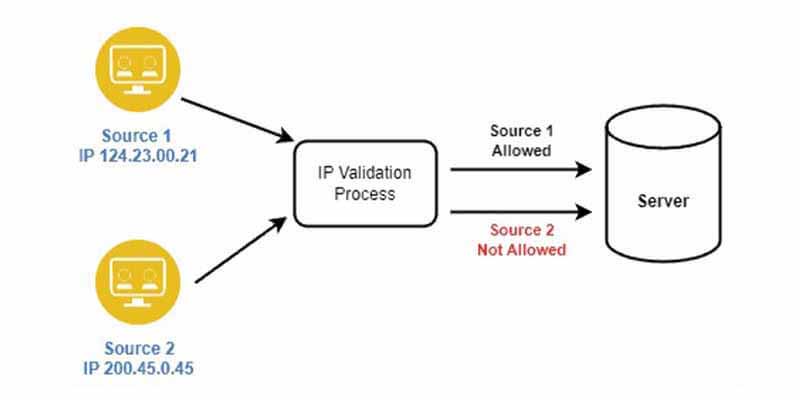
Implementing IP filtering involves setting up rules to allow or block access based on users’ IP addresses. It’s like having a bouncer at a party checking invitations; only those with approved IPs get in. For example, a company might use IP filtering to allow only employees to access certain internal resources from within the office network.
Session timeouts are like automatically logging out of a website after a period of inactivity. It’s similar to locking your phone when you’re not using it to keep it secure. For instance, a banking website might log you out after 10 minutes of inactivity to prevent someone else from accessing your account if you forget to log out yourself. These measures add extra layers of security to protect against unauthorized access and session hijacking.
Implementing Two-Factor Authentication:
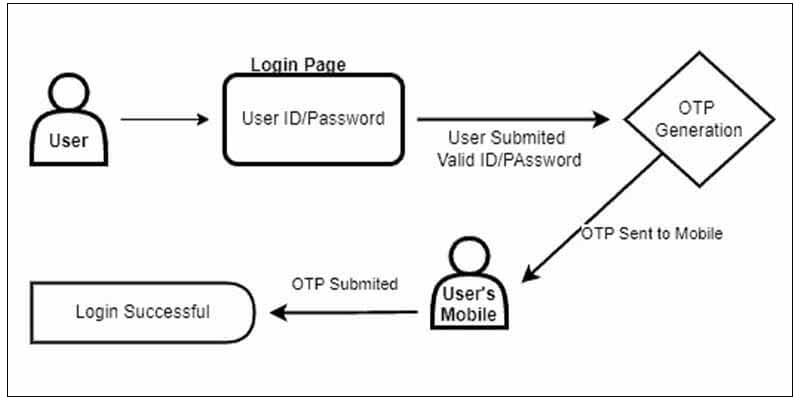
Implementing Two-Factor Authentication (2FA) adds an extra layer of security beyond just a password. It’s like having a secret code sent to your phone when you log in, besides typing your password. For example, after entering your password on a website, you might receive a text message with a temporary code that you also need to input to complete the login process.
This additional step makes it much harder for hackers to gain unauthorized access, even if they somehow manage to obtain your password. It’s like having two locks on your front door instead of just one, providing stronger protection for your accounts and sensitive information.
By implementing these preventive measures, organizations can significantly reduce the risk of session hijacking and enhance the security of their online systems and user data.
How To Prevent Session Hijacking
Knowing how to recover from a session hijacking attack is truly important if you are a webmaster. These simple techniques can help you out from the greater danger. You can avoid such vulnerabilities easily by applying the strategies.
However, recovering from a session hijacking attack requires swift action to regain control of compromised accounts and mitigate potential damage. Here’s a step-by-step guide:
Terminate Active Sessions: Immediately log out of all active sessions on the affected accounts. This action helps prevent further unauthorized access by terminating the hijacked session.
Change Passwords: Reset passwords for all affected accounts using strong, unique passwords. Ensure that the new passwords are not easily guessable and are different from any previously used passwords.
Enable Two-Factor Authentication (2FA): Implement 2FA on all relevant accounts if not already enabled. This additional layer of security helps prevent unauthorized access even if the attacker has obtained the password.
Review Account Activity: Thoroughly review recent account activity to identify any suspicious or unauthorized actions taken by the attacker. Look for changes in account settings, unauthorized transactions, or unusual login locations.
Contact Service Providers: Notify relevant service providers or website administrators about the session hijacking incident. They may be able to assist with account recovery procedures or provide additional security measures.
Scan for Malware: Conduct a thorough malware scan on all devices used to access the compromised accounts. Remove any detected malware or suspicious software to prevent further compromise.
Monitor Account Activity: Monitor account activity closely in the following days and weeks for any signs of continued unauthorized access or suspicious behavior. Report any further incidents to the appropriate authorities or service providers.
Educate Users: Educate users about the risks of session hijacking and provide guidance on best practices for securing their accounts, such as using strong passwords, enabling 2FA, and avoiding suspicious links or downloads.
By following these steps promptly and thoroughly, individuals and organizations can recover from a session hijacking attack and strengthen their defenses against future incidents.
You can take help from WPSafe.ai to remove any kind of malware or virus from your site. Scan your site now.
Frequently Asked Questions:
Q1: What is session hijacking and why is it a concern for online security?
A1: Session hijacking is a cyberattack where an unauthorized person intercepts and takes control of an active session between a user and a website. It’s concerning because it can lead to unauthorized access to sensitive data and actions on the user’s behalf.
Q2: How can I prevent session hijacking?
A2: Implementing HTTPS encryption, using secure cookies, and employing strong authentication methods like two-factor authentication are effective ways to prevent session hijacking.
Q3: Does using public Wi-Fi increase the risk of session hijacking?
A3: Yes, public Wi-Fi networks are vulnerable to session hijacking attacks because they often lack encryption. It’s crucial to avoid accessing sensitive accounts or sharing personal information over public Wi-Fi to reduce the risk.
Q4: Is regularly updating software important for preventing session hijacking?
A4: Absolutely. Software updates often include security patches that address vulnerabilities exploited by attackers for session hijacking. Keeping your software up-to-date helps maintain strong defenses against such attacks.
Q5: Can using a virtual private network (VPN) help prevent session hijacking?
A5: Yes, VPNs encrypt your internet traffic, making it difficult for attackers to intercept and hijack sessions. Using a reputable VPN service adds an extra layer of security, especially when accessing the internet over public Wi-Fi networks.
Q6: Are there browser extensions or plugins that can help prevent session hijacking?
A6: Yes, there are browser extensions available that offer additional security features, such as cookie management and script blocking, which can help prevent session hijacking. However, it’s essential to choose reputable extensions from trusted sources to avoid potential security risks.
Q7: How often should I review my account activity to detect potential session hijacking attempts?
A7: It’s a good practice to regularly review your account activity for any suspicious or unauthorized actions. Depending on the sensitivity of your accounts and your online activity, reviewing your account activity weekly or even daily can help detect and respond to session hijacking attempts promptly.
Wrapping Up:
In conclusion, safeguarding against session hijacking is paramount for online security. By implementing measures such as HTTPS encryption, strong authentication methods, and regular software updates, individuals and organizations can significantly reduce the risk of unauthorized access and protect sensitive data. How To Prevent Session Hijacking ensures a safer online experience, empowering users to navigate the digital landscape with confidence and peace of mind.
Image Credit:
